 2021 has shattered economies of almost every sector with the pandemic wreaking havoc worldwide. On top of it, most industries have had to contend with malicious cyber activities, as ransomware threats are some of the most challenging cyber threats organizations worldwide have to deal with. Almost every industrial sphere, including government departments, the education sector, the retail sector, and manufacturing establishments, has felt the impact of ransomware at some point.
Unit 42, the threat research team of Palo Alto Networks, has compiled a comprehensive 2022 Ransomware Threat Report highlighting ransomware activity worldwide. The report can help organizations perceive the seriousness of the situation and take remedial steps to prevent becoming victims of such cyber attacks and therefore jeopardizing the confidentiality, integrity, and availability of valuable information assets.
2021 has shattered economies of almost every sector with the pandemic wreaking havoc worldwide. On top of it, most industries have had to contend with malicious cyber activities, as ransomware threats are some of the most challenging cyber threats organizations worldwide have to deal with. Almost every industrial sphere, including government departments, the education sector, the retail sector, and manufacturing establishments, has felt the impact of ransomware at some point.
Unit 42, the threat research team of Palo Alto Networks, has compiled a comprehensive 2022 Ransomware Threat Report highlighting ransomware activity worldwide. The report can help organizations perceive the seriousness of the situation and take remedial steps to prevent becoming victims of such cyber attacks and therefore jeopardizing the confidentiality, integrity, and availability of valuable information assets.
Source of the Report
Unit 42 relied mainly on the following two sources while generating the report:- Actual cases handled by the unit that provided a realistic view of the extensive range of threat actors.
- Analysis of leak sites that included malicious activities like multi-extortion to coerce or even threaten victims to pay the ransom.
Crucial Statistics from the Report
Before going into the detailed summary of the 2022 Ransomware Threat Report, here are some important statistics to better understand the scope of this matter.- The average ransom demand grew 144%, from $900K in 2020 to 2.2M in 2021.
- Simultaneously, the average ransom payment grew to $541K, a 78% increase from 2020.
- The US remains the most targeted country with 60% of ransomware cases in 2021, followed by the European, Middle lEast, and African (EMEA) countries with 31%. The Asia-Pacific region was in the third position with 9% of ransomware cases.
- Professional and legal services were the most targeted sectors, with 1,100 victim organizations, followed by the construction sector, with nearly 600.
 (Data Source: Palo Alto RansomwareThreat Report 2022)
(Data Source: Palo Alto RansomwareThreat Report 2022)
Understanding Ransomware
Ransomware is a specialized malware used to paralyze organizational functioning by encrypting its data to extort money. They usually demand ransom in cryptocurrency to prevent establishing a trail. When the ransom is received, , the malicious actors provide the decrypting code, allowing the organization to retrieve its information assets. Usually, threat actors use social engineering tactics like phishing emails to introduce malware into the target’s information systems. This scheme relies on the victims clicking on the malicious links, and therefore accidentally downloading the ransomware into the information system. Once the malware is installed, it takes over the functioning and stops access to critical data by encrypting it.Change in Tactics
Malicious actors employed more sophisticated tactics, such as the ones mentioned below, in 2021 compared to 2020, as they widened their scope of attacks.- Ransomware-as-a-Service: Malicious actors started offering RaaS packages to anyone interested in launching an attack. It lowered the technical barrier for non-experts to access information systems and thus enhanced the speed of cyberattacks.
- Multi-Extortion: Besides asking for the regular ransom, malicious actors started blackmailing their victims, threatening to leak critical information and launching DDoS attacks to extort ransom quickly.
- The Exploitation of Zero-Day Vulnerabilities: Threat actors started taking advantage of zero-day vulnerabilities such as Log4Shell to launch ransomware and continued to exploit organizations that failed to patch them properly.
The Overall Ransomware Landscape
Below are the critical emerging trends concerning the transformation of the overall ransomware landscape over the years, according to the Palo Alto Networks Report. It can help organizations formulate effective defense and incident-response strategies.Ransomware Actors’ Psychology
Ransomware has evolved over the years. Here are some latest psychological traits observed among ransomware actors.- Exploit Shortcuts: Today, ransomware actors hire the services of brokers who provide access to information systems, as it saves them time and effort. It has increased the scope of attacks as non-expert attackers can easily drop malware into an already compromised environment.
- Go to Extremes: They have started using anonymized services like TOR (The Onion Router) to make it challenging for law enforcement authorities to track their activities and identify the indicators of compromise (IoC).
- Innovation: Ransomware groups now use updated ransomware variants instead of standalone malware. For example, HelloKitty uses Linux and BlackCat uses Rust to launch attacks quickly.
Ransomware Trends for 2022
Consequent to the innovative tactics used by ransomware actors, the trends for 2022 have changed considerably, as is evident below.- Increase in Victim Shaming: Ransomware actors have increasingly started using techniques like double-extortion to prevent organizations from restoring data from backup alternatives and resuming operations. Threat actors like Black Matter, Grief, and Hive used such tactics. BlackCat and Suncrypt even use triple extortion tactics like threatening to launch DDoS attacks besides leaking confidential and sensitive information. Over 2,500 victims were publicly shamed in 2021.
- Increase in RaaS: Malicious actors have now started offering Ransomware-as-a-Service to anyone who wants to hire them. Thus, it has widened the scope for ransomware attacks as individuals with little knowledge of ransomware can launch cyberattacks. Nearly 56 RaaS groups have been identified, and the number is expected to grow in 2022.
- Exploiting Zero-Day Vulnerabilities: Ransomware actors have increased, exploiting zero-day vulnerabilities as an initial compromise vector. Malicious operators used nearly 42 such instances in 2021. Unpatched vulnerabilities are serious, as observed in the Kaseya attacks by REvil. Organizations should take note and act accordingly to plug such gaping holes instantly.
The Emergence of Ransomware Gangs
2021 was the year of ransomware gangs, and thirty-five have been identified recently. Trends show that some groups lie low for a while before resurfacing to launch more powerful attacks. Conti was the most active ransomware gang, responsible for 15.5% of ransomware activity. REvil was the second with 7.1%, followed by HelloKitty and two others, each with a 4.8% share of the attacks. (Data Source: Palo Alto RansomwareThreat Report 2022)
Below passages will give a brief idea of the major gangs and their activities:
(Data Source: Palo Alto RansomwareThreat Report 2022)
Below passages will give a brief idea of the major gangs and their activities:
- Conti: Conti was the most active ransomware gang in 2021, with an initial ransom demand of $50K. It rose substantially to an average of $1.78M for the year, with the highest ransom demanded at $3M. The gang has affected more than 600 organizations since 2020, including law enforcement agencies, construction projects, emergency services, and hospitals.
- REvil: REvil, also known as Sodinokibi, had the highest activity in 2020. But it dropped down to second place in 2021. However, their average ransom has increased to approximately $2.2M, and their highest demand has been $5.4M. REvil is a major provider of RaaS.
- BlackCat: BlackCat is another main RaaS provider notorious for observing and soliciting affiliates in cybercrime forums. It allows affiliates to retain 80% to 90% of the ransom while keeping only the remaining 10 to 20% to themselves. The group attacked various sectors, including construction, retail, insurance, transport, professional services, automotive establishments, and pharmaceuticals.
- Other Ransomware Actors: Other big ransomware names include AvosLocker, Hive, HelloKitty, LockBit 2.0, Mespinoza, and eChOraix.
Initial Ransom Amount Vs. Payment Amount
Generally, there is a difference between the initial ransom amount demanded and the payment amount due to various negotiations between the attackers and the victims. In one instance, BlackCat demanded a payment of $9M and even received $8.5M. On average, the ransom payout in 2021 was around 42.87% of the initial ransom demand. (Data Source: Palo Alto RansomwareThreat Report 2022)
(Data Source: Palo Alto RansomwareThreat Report 2022)
Multi-Extortion Techniques
Earlier, ransomware actors used to launch their attacks and send the ransom note to the victim. Once the victim pays the ransom, the attackers provide the decryption key enabling the target to access its data and resume its operations. However, this method had its shortcomings. The ransomware attacks do not exfiltrate data but only encrypt them. So, organizations having a separate backup could always restore the data and avoid paying the ransom. Now, the ransomware actors have upgraded their modus operandi by exfiltrating data and threatening the victim about releasing it in the public domain, which could lead to massive data breaches and loss of reputation. Thus, there is a double extortion demand. One is the regular ransom for obtaining the decryption key, and the other is for the attackers’ refraining from exposing the data to the public. Such a scenario is known as double extortion. Maze popularized this method in 2019. As mentioned earlier, Suncrypt and BlackCat threatened the victims to launch DDoS attacks on their organizations’ infrastructures if the ransom negotiation failed. Besides, they threatened to leak critical information on the dark web and taint their reputation. This type of extortion is known as triple extortion.Critical Insights from Ransomware Leak Sites
Conti and LockBit 2.0 were the two most significant ransomware gangs to indulge in leaking critical information and leveraging double-extortion threats. Compared to 2020, there is an 85% increase in public postings involving 2,566 victims. Conti accounted for 511 postings, and LockBit, for 406.Most Targeted Sectors
Ransomware actors did not spare any sector in 2021. The most targeted sector was the Professional and Legal Services industry, followed by the Construction industry. One reason is that many organizations in these sectors do not run on up-to-date software, becoming more prone to cyberattacks. Besides, the malicious actors know that these industries lose their reputation quickly if their information systems are compromised, as they often provide services using their dedicated software. These sectors also work on tight deadlines, increasing the chances of paying the ransom amounts.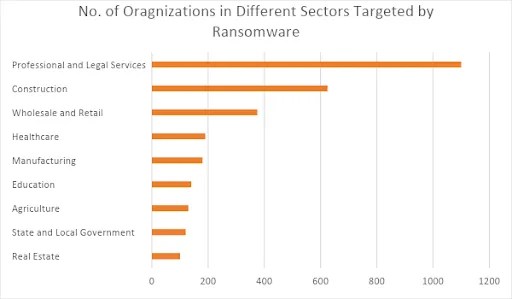 (Data Source: Palo Alto RansomwareThreat Report 2022)
(Data Source: Palo Alto RansomwareThreat Report 2022)
Rebranding of Ransomware Gangs
Many ransomware gangs vanished from the scene following failures due to flaws in their ransomware. Many resurfaced later as new brands with more sophisticated technology. Attacker groups also lie low due to pressure from law enforcement agencies, internal struggles, and peer competition.Ransomware in the Cloud
Today, organizations increasingly store their data and function in a cloud environment. However, the dynamic workloads in a multi-cloud environment can be challenging. Though there were no major instances of ransomware attacks on the cloud, it is only a matter of time, considering the valuable information assets stored there. The example of Log4j vulnerability highlights the need to secure the cloud environment and maintain a robust vulnerability management program. Trends show that ransomware actors use cloud APIs to access and encrypt crucial information assets. Therefore, organizations should strengthen these aspects and use strict IAM (Identity and Access Management) practices to secure access to these APIs.Ransomware Costs
Besides the financial loss of paying the ransom, the affected organizations suffer from other collateral damage, such as downtime, disruptions, reputational loss, time loss in recovery, legal expenses, and loss of information assets. The Palo Alto report states that 58% of organizations preferred paying the ransom, whereas 14% spent money more than once.Recovery Time
Studies show that 41% of organizations recovered within one month of the ransomware attack, whereas 20% of victims recovered within three months. And while 29% took more than three months, 9% even took more than five to six months for recovery. (Data Source: Palo Alto RansomwareThreat Report 2022)
(Data Source: Palo Alto RansomwareThreat Report 2022)
Recommendations to Remain Resilient to Ransomware Attacks
Finally, Unit 42 recommends the following actions for organizations to stay more resilient to ransomware attacks.- Keep your information systems updated to take care of the evolving threat landscape.
- Evaluate and analyze the impact of compromising your information assets.
- Assess your readiness levels and have a clear incident response plan.
- Implement and follow a Zero Trust policy.
- Identify your exposed information assets.
- Protect your systems from known and unknown threats.
- Automate your systems and use secure cloud workloads.
- Use IR retainers (contracts with incident response experts) to reduce response time.
Final Words
Ransomware has gradually become one of the worst cybersecurity threats in recent times. The situation can worsen in the forthcoming years, especially with more organizations working online. However, one can take remedial measures and enhance vigilance to prevent becoming a victim of a ransomware attack. The 2022 Ransomware Threat Report from Palo Alto Networks provides comprehensive information on ransomware trends and highlights the significance of treating this cyber threat with utmost seriousness. Today, ransomware actors don’t just target bigger organizations, but everyone, including small businesses and even individuals, is on their radar. Thus, one needs to have adequate preventive measures to ensure threat actors cannot get their hands on the organization’s information assets in the first place. Besides, there must be a business recovery and continuity plan in place for the worst-case scenario when ransomware actors are able to infiltrate the information systems.References
- Minutes, 10. (2021, December 12). Update: Prisma Cloud addresses Log4Shell: CVE-2021-44228, CVE-2021-45046 mitigations. Palo Alto Networks Blog. https://www.paloaltonetworks.com/blog/prisma-cloud/log-4-shell-vulnerability/
- Santos, D. (2022, June 3). Understanding REvil: REvil threat actors may have returned (updated). Unit 42. https://unit42.paloaltonetworks.com/revil-threat-actors/
- (N.d.). Paloaltonetworks.com. Retrieved August 6, 2022, from https://www.paloaltonetworks.com/content/dam/pan/en_US/assets/pdf/reports/2022-unit42-ransomware-threat-report-final.pdf
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About vRx
vRx is a consolidated vulnerability management platform that protects assets in real time. Its rich, integrated features efficiently pinpoint and remediate the largest risks to your cyber infrastructure. Resolve the most pressing threats with efficient automation features and precise contextual analysis.



